MSSQL Attacks Skyrocket as Overall Threat Activity Jumps Nearly 50% in November 2025
HoneyDB Monthly Update
Overall cyberattack event volume, as tracked by HoneyDB honeypots, saw a dramatic increase in November 2025 compared to the previous month. This surge signals a significant escalation in automated threat activity across the globe. This analysis breaks down the key numbers and reveals a critical shift in attacker priorities: a move toward high-volume, automated attacks targeting the core data and communication services that power modern business.
November 2025: The Raw Numbers
By the Numbers
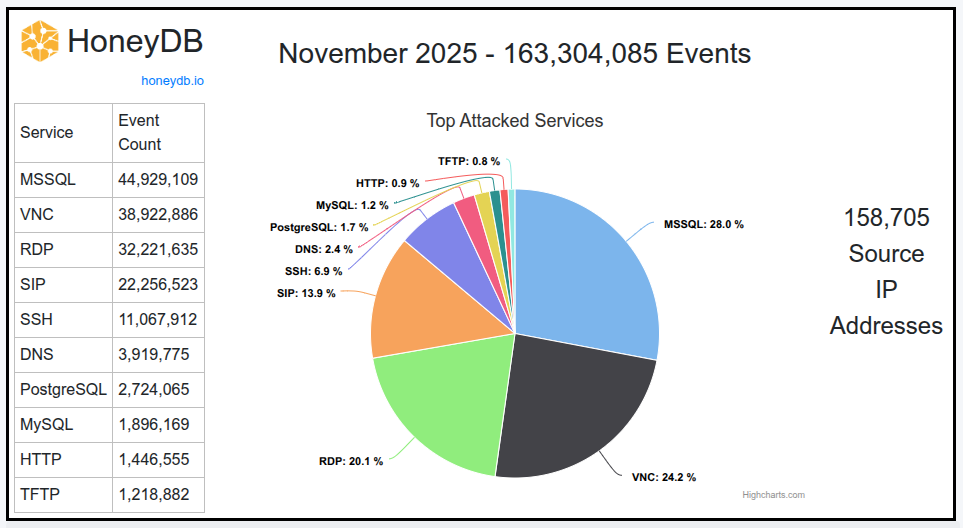
Total Attack Events: 163,304,085
Total Attacking Hosts: 158,705
Top 3 Most Targeted Services
MSSQL: 44,929,109
VNC: 38,922,886
RDP: 32,221,635
The Big Story: What Changed from October?
The top-level numbers only tell part of the story. A month-over-month comparison reveals several critical shifts in attacker methodology and targeting. While the explosion in MSSQL traffic is the month’s headline, seasoned defenders will note that brute-force attacks against remote access protocols like VNC and RDP remain a constant, high-level threat, occupying the #2 and #3 positions respectively. The key takeaways below highlight where attacker priorities are changing most dramatically.
Takeaway 1: MSSQL Attacks Explode, Taking the Top Spot
The most dramatic shift was in attacks targeting Microsoft SQL Server (MSSQL). After ranking third in October with 23,931,998 events, MSSQL jumped to the #1 position in November with a staggering 44,929,109 events. This represents a nearly two-fold increase in attack traffic against a single, critical database service. This shift suggests that threat actors are moving beyond opportunistic remote access attacks and are now prioritizing reconnaissance and direct assaults on known data repositories. This focus on databases is not isolated to MSSQL; PostgreSQL also remained a Top 10 target, reinforcing the trend of attackers hunting for data-rich environments.
Takeaway 2: Overall Attack Volume Spikes by Nearly 50%
Total observed attack events grew from 110,439,876 in October to 163,304,085 in November—a massive 48% increase in just one month. This spike in volume was not matched by a similar increase in the number of unique attackers; the count of attacking hosts rose only slightly from 156,550 to 158,705. This disparity strongly suggests that the increase is driven by more intense, high-volume automated attacks originating from a relatively stable pool of compromised machines or malicious infrastructure.
Takeaway 3: Don’t Overlook SIP
Another significant surge occurred in attacks targeting the Session Initiation Protocol (SIP), a foundational protocol for VoIP and online communications. SIP-related events more than doubled, jumping from 9,764,653 in October to 22,256,523 in November. This indicates that attackers are increasingly targeting communication systems, likely for toll fraud, eavesdropping, or denial-of-service attacks.
Conclusion: What’s Next?
The data for November 2025 paints a clear picture: a sharp escalation in automated attacks, with a renewed and intense focus on the backbones of modern business—database services like MSSQL and communication protocols like SIP. As attackers intensify their focus on data and communication infrastructure, how should organizations re-evaluate their perimeter defenses for 2026?
Explore the Data Yourself
To dive deeper into this threat intelligence, visit honeydb.io. You can sign up to access this data via the API or contribute to the project by running your own honeypot sensor.