The Database Siege: MSSQL Activity Doubles as Attackers Pivot from Access to Data in January 2026
HoneyDB Monthly Update
Each month, we analyze global honeypot data to track shifts in the internet’s background “noise” of scans, exploit attempts, and automated reconnaissance. These patterns reveal when routine activity escalates into something more deliberate. January 2026 stood out immediately—showing a sharp expansion in attacker infrastructure, a clear protocol pivot, and an aggressive surge in database-targeted activity that signals a meaningful shift in the threat landscape.
The Global Pulse of Cyber Activity
In the vast, interconnected expanse of the modern internet, there is a constant “background radiation” of automated scans, exploit attempts, and reconnaissance. This ambient noise is not random; it is the heartbeat of a global ecosystem of botnets and threat actors. Understanding these shifting patterns is critical for cybersecurity professionals, and HoneyDB’s global data provides a unique window into this evolution. By monitoring these trends month-over-month, we can identify when the threat landscape moves from its baseline into a state of heightened escalation.
To gain this visibility, researchers utilize honeypots—decoy systems designed to be probed and attacked by malicious actors. These “digital canaries” serve as an early warning system, capturing the tactics and targets of attackers without risking production infrastructure. As we analyze the data from the opening month of 2026, these sensors have signaled a dramatic and focused shift in global adversarial intent.
January 2026: A Month of Massive Escalation
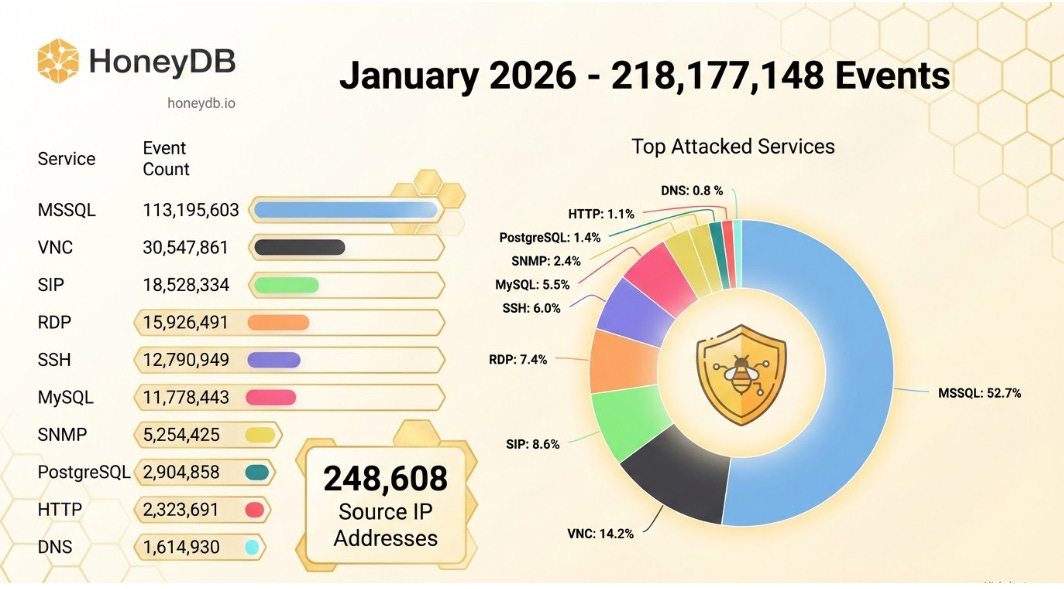
January 2026 was characterized by an extraordinary surge in automated threat activity, marking a high-pressure start to the year for network defenders. During this period, HoneyDB sensors logged a staggering 218,177,148 total events originating from 248,608 unique remote hosts.
The sheer scale of these figures—nearly a quarter of a million unique hosts actively probing the internet—highlights the intensity and expansion of modern threat infrastructure. However, the activity was not evenly distributed across all services. The top targeted protocols in January were:
• MSSQL (Microsoft SQL Server): 113,195,603 events
• VNC (Virtual Network Computing): 30,547,861 events
• SIP (Session Initiation Protocol): 18,528,334 events
While SIP remains a primary target, it is notable that it saw a slight decline from its December volume of 18.7 million events. This outlier suggests that while the broader internet is under increased pressure, attackers are becoming more surgical in where they direct their resources.
The Shift: Comparing December to January
Strategically, month-over-month comparisons are vital for identifying sudden shifts in attacker behavior or the deployment of new toolsets. By synthesizing the data between December 2025 and January 2026, we see a clear and aggressive growth trend. Total event volume grew from approximately 165 million to over 218 million. Most significantly, the number of unique remote hosts increased by over 50%, rising from 163,633 to 248,608. This suggests a massive expansion in the botnet infrastructure used to facilitate these attacks.
Perhaps the most telling story is the “Protocol Pivot.” The data reveals a notable decline in specific access-oriented services:
• RDP (Remote Desktop Protocol): Dropped significantly from 28.2 million to 15.9 million events.
• DNS (Domain Name System): Activity was effectively halved, falling from 3.2 million to 1.6 million events.
This suggests a strategic transition in the threat landscape. While overall activity is rising, attackers appear to be moving away from general “Initial Access” vectors like RDP and DNS and are instead focusing their energy on the “Post-Exploitation” and “Exfiltration” phases of the kill chain.
Analysis: The MSSQL Explosion and Infrastructure Awareness
The most impactful differentiator in the January data is the massive explosion in MSSQL activity. In December, MSSQL was already a top target with 53.3 million events; in January, that number skyrocketed to over 113 million events. MSSQL activity more than doubled in just 31 days and now accounts for more than half of all recorded events globally.
From a storyteller’s perspective, the “Why” is clear: attackers are targeting the “Crown Jewels.” By brute-forcing MSSQL sa (system administrator) accounts, actors can move directly to data exfiltration or the deployment of ransomware within a database environment.
Furthermore, the sudden entry of SNMP into the top 10 (over 5.2 million events) and the exit of FTP indicates a more “infrastructure-aware” adversary. The surge in SNMP—often part of the internet’s background radiation—suggests a new wave of botnets scanning for network misconfigurations to gain a deeper understanding of target environments before an attack is even launched.
Strategic Takeaways for Defenders:
• Prioritize Database Hardening: With MSSQL representing over 50% of global honeypot traffic, organizations must prioritize MSSQL log monitoring and aggressive account lockout policies for the remainder of Q1.
• Audit Network Management: The rise of SNMP scanning suggests attackers are seeking network topology data. Ensure SNMP strings are changed from defaults and access is restricted to authorized IPs.
• Monitor the Pivot: As attackers move away from RDP and toward data-hosting services, shift your internal monitoring focus from simple perimeter access to lateral movement and database query anomalies.
Final Thought
As we move further into 2026, we must ask: does the MSSQL surge represent a temporary spike or a new baseline for the year? The speed at which these trends evolve is a stark reminder that defenders must be as agile as the adversaries they face.
Explore the Data Yourself
To stay ahead of these shifts, we invite you to explore this data in detail. Visit honeydb.io to access our comprehensive threat data via API for your own research. You can also help defend the perimeter by contributing to global intelligence—consider running your own honeypot sensor and providing the community with more “digital canaries” to watch the horizon.